If there is anything sure about the future of IT, it’s that there will be more security threats, increasing complexity and greater pressure to provide IT services 24x7. And that applies to everyone - whether you are building a new application or working with the same application that has been running on your IBM Power Systems for over 20 years.
The IBM Power Systems security assessment and the health check are proactive measures that scan your systems for a broader range of security settings, risks and overall performance status, including health, currency, backup and disaster recovery. In this blog, let’s take a closer look at the security assessment. In the following blog post, we will look at IBM Power Systems Health Check.
What is IBM Power Systems Security Assessment?
The Security Assessment for IBM Power Systems is designed to identify security vulnerabilities that expose your organization to avoidable risk. The assessment scans your operating system environment (whether it is IBM i, AIX or Linux), applications, settings, users profiles and permissions. The assessment results will give you a detailed report of your current security status and remediation recommendations to help you achieve your security and compliance goals.
Who should consider a security assessment?
Anyone looking for comprehensive security analysis on Power Systems virtualization and operating systems. More specifically, if you have requirements in any of the following areas, you should consider doing a security assessment:
-
run PowerVM, AIX, IBM i, or Linux virtual machines and want to identify security vulnerabilities
-
need to benchmark your security and compliance processes against the latest industry best practices
-
need advice on standard, secure operating system images on IBM Power Systems
What is the process of a security assessment?
1. Step One - Data Collection: In this step, we provide you with an agent that can be run at any time for a simple gathering of all the required settings and attributes. Please note that the information collected here is metadata and settings only; we do not collect nor examine any actual data.
2. Step two - Data Analysis and Report Generation: Based on the data collected, we prepare a set of three deliverable reports:
-
Executive summary – this is an overall security state that gives you a weighted list of recommended enhancements
-
Complete report – this report contains detailed information about what was found and recommended remediation methods
-
Comparative matrix – this section has colour-coded data points comparing your assessed systems
3. Step Three - Result Presentation and Q&A: At this step, we will schedule an online or face-to-face workshop session with your team to cover the results, major risks, discuss remediation methodologies and provide you with a chance to ask any questions.
What you can expect from the security assessment:
-
Security assessments include an executive summary presentation, a security matrix, and a detailed report with recommendations on risk remediation.
The following is a sample report that shows colour-coded data points:
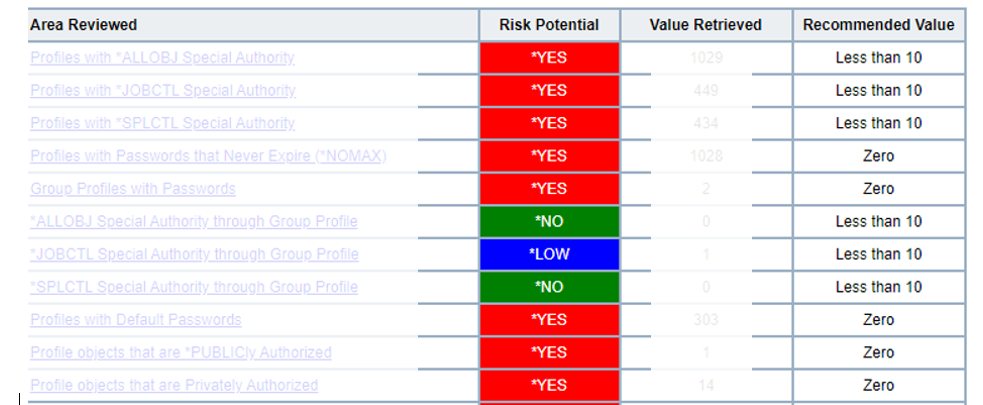
-
Security remediations include planning documentation, project guidance, and system hardening recommendations.
-
Skills enablement and guidance on best practices for managing security and compliance on IBM i, including Security and Compliance tools for IBM i.
Benefits for IBM Power Systems Security Assessment:
-
Get a comprehensive, independent report to help you identify potential security vulnerabilities and risks.
-
Get advice on best practices from an experienced IBM security consultant focused on the operating systems and hypervisor security
-
Gain confidence that you’re using best practices to protect your sensitive data
-
Help you address issues that affect IT compliance and governance standards
-
Justify investments needed to enhance your internal security practices and procedures
As security is a constantly changing area, it's a good to do Security Assessment annually to understand the risks in your current setup and configuration. Blair Technology Solutions is an IBM Platinum Business Partner with a strong foundation in IBM Power Systems. We are currently offering a one-time, one LPAR offering for an automated security scan and report for your IBM Power Systems. Contact us to request your complientary IBM Power Systems Security Assessment today.









