What is Cyber Insurance?
Cyber insurance is a specialty insurance product intended to protect businesses from risks relating to information technology infrastructure and activities. As big and small organizations see a surge of cyber-attacks in the past few years, many are turning to cyber insurance, hoping to get some coverage if a cyber incident happens to them. This includes but is not limited to fine charges, compliance, hardware and software repairs, and third-party compensation, among others.
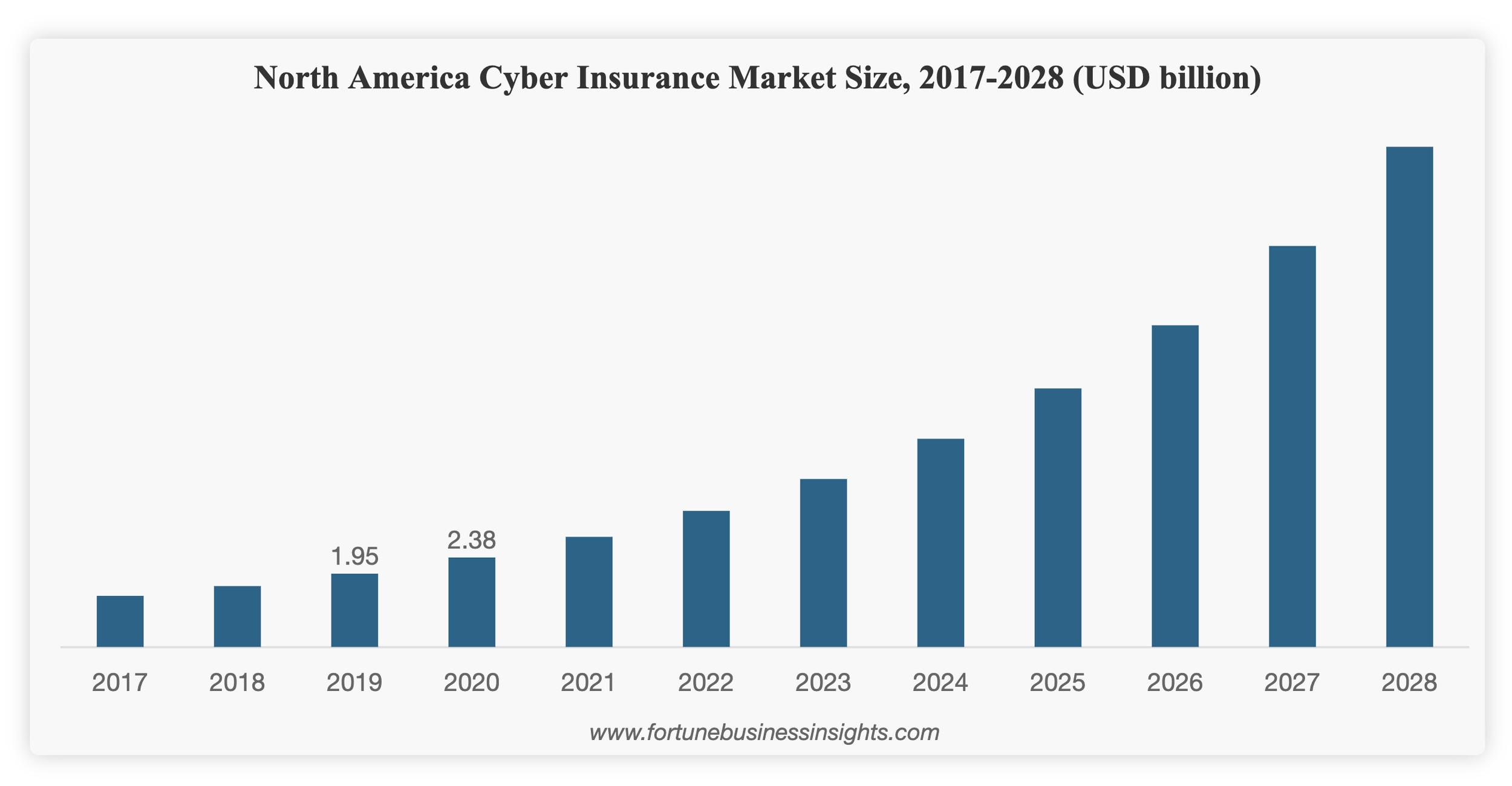
According to CIRA’s 2021 Cybersecurity Survey, six out of ten Canadian organizations with more than 50 desktops have cybersecurity insurance coverage; three in ten have a cybersecurity-specific policy. Globally, the cyber insurance market size is projected to grow from 7.60 billion USD in 2021 to 36.85 billion USD in 2028 at a CAGR of 25.3% in the 2021-2028 period. The following chart from Fortune Business Insights shows the growth prediction:
Are you Qualified for Cyber Insurance?
If you have ever shopped for property insurance, you know that the insurance company is going to ask you many questions. The same is true for cyber insurance. If you consider a cyber-attack as a “digital fire” to your business, it is not difficult to understand why cyber insurers will ask you questions like “Do you have multifactor authentication? What is your Incident Response Plan? What is your backup plan?”
The reality is that not every organization is qualified to get cyber insurance and often, if they pass the qualification, they will be surprised at the high premiums they need to pay for cyber insurance.
Five Requirements Needed to Obtain Cyber Insurance
According to industry experts, most insurance requirements fall into basic cybersecurity measures, and at minimum include:
1. Backup
Data backup is the most important step to ensure quick recovery from cyber security incidents such as ransomware or malware as well as other disruptions such as natural disasters, equipment failure etc. Organizations should develop their own backup strategy and schedule and follow best practices. These include increasing backup frequency, following the 3-2-1 rule (3 data copies – 1 primary and 2 backups, 2 types of storage, and 1 off-site storage), and testing your backup and recovery regularly to make sure you are fully prepared when the real disruption occurs.
2. Multifactor Authentication (MFA)
Organizations should implement two-factor authentication wherever possible; especially for access to important accounts, such as financial accounts, system administrators, cloud administration, and other privileged users. These methods combine the use of a password with a one-time code, such as an app-generated code or an automated text message or phone call sent to a pre-registered phone number.
3. Patching
Malicious individuals or groups are constantly looking to exploit newly published vulnerabilities to attack computers, servers, and networks with these weaknesses. That’s why it is recommended to only run current, vendor-supported operating systems for which security patches are made available in a regular and timely fashion. Available security patches, upon release by the vendor, should be tested and then applied to production systems on a schedule appropriate to the severity of the risk they mitigate.
4. Cyber Awareness Training for Employees
Security awareness training is the best way to begin protecting your organization from the ever-changing threat landscape. By providing your staff with the knowledge required to recognize and react to cyber threats, you are creating a shift in employee mindset and implementing behavioural change, which will lead to reduced human error and an improved cybersecurity posture.
5. Incident Response Plan
Cybersecurity incidents never happen at a convenient time; and when your business is caught in a worst-case critical incident and time is against you, it will be too late to come up with a incident response plan. Having a clearly-defined Incident Response Plan will provide the instructions and procedures that you can use to identify, respond to, and mitigate the effects of a cyber incident.
Blair Technology Solutions provides Incident Response Services that give you immediate, 24x7 real-time management and guidance to effectively assess, investigate, contain, and remediate severe security incidents. Contact us to schedule a discovery call.









